Quick Links
-
How This Smishing Attack Disables iMessage Security
-
What You Can Do If You Already Responded
A dangerous smishing campaign is targeting Apple iMessage users, using social engineering to disable the messaging service’s built-in phishing protection. The attack could expose millions of users, but you can stay safe by changing one security feature.
How This Smishing Attack Disables iMessage Security
Apple’s built-in security protection blocks links sent over iMessage if the text is from an unknown sender. This is to protect users from exposure to malicious links. Cybercriminals have found a loophole to bypass this feature by tricking you into disabling this phishing protection.
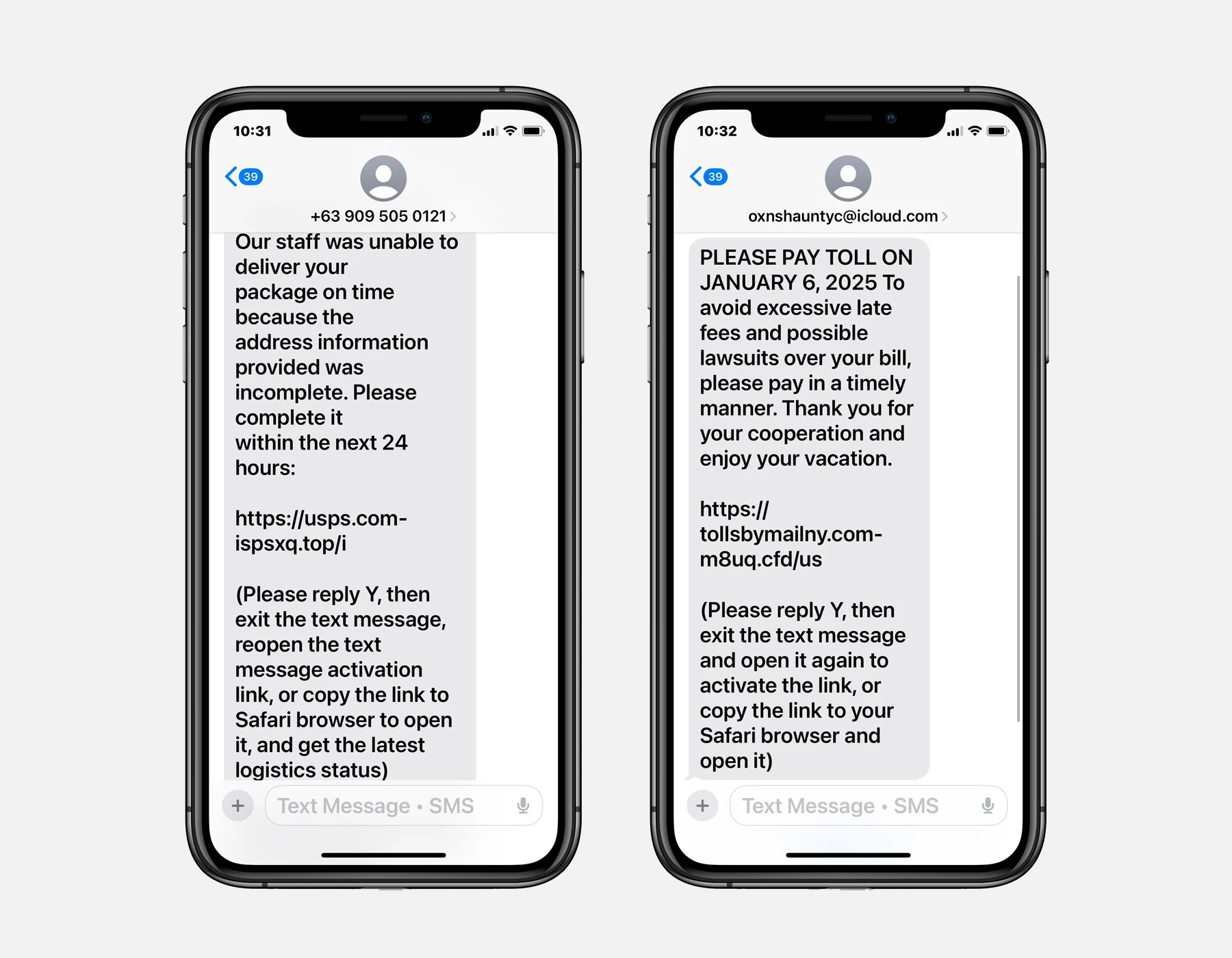
Attackers are sending fake alerts that require iMessage users to reply. These come in the form of a fake delivery alert or a fake unpaid toll message. The message asks users to reply with “Y” (yes) or “N” (no) to accept or reject the delivery. Replying tells iMessage that this number is known to you, so links become enabled.
Bleeping Computer reports that the message also includes instructions to “Exit the text message, reopen the text message activation link, or copy the link to a Safari browser” to get the latest delivery status or pay the toll fee. The link takes users to a phishing site where their personal and financial information is stolen and later used for identity theft, credit card fraud, and other attacks.
Since people are used to replying STOP, YES, or NO to confirm or cancel legitimate appointments or alerts via text, attackers exploit this to make users think replying is harmless. Even if you don’t click on the link, replying tells attackers that you respond to smishing texts, making you a target for future attacks.
How to Protect Yourself
Do not reply to text messages from numbers you don’t recognize because this disables Apple’s built-in security protection, especially if you receive a message about a package you are not expecting or a fine you are unfamiliar with. Always treat links sent by unknown sources as malicious: do not click. There are also other ways to spot a smishing text.
If you are unsure if you have a package or a fine and fee to pay but still want to check, close iMessage and open the official company’s website using your browser. Contact their customer service to verify the information. You can also log into your account through their website or app. Do not visit the site using the link from the message.
Be wary of messages that pressure you to take “immediate” action, offer a “limited time offer,” or threaten you with negative consequences if you don’t respond immediately. Most phishing scams are designed to make you act first before you think. This makes you hand them your information before realizing you’ve been scammed.
What You Can Do If You Already Responded
If you have already responded or followed the instructions by the attackers before realizing that this is a scam, there are still ways to mitigate it.
First, block the number immediately to prevent them from sending you further messages. Then, change your accounts’ passwords and enable multifactor authentication (MFA).
If you have already given your financial information, call your bank immediately. The bank can freeze your account, cancel your credit card, and issue a new one.
If you’ve given hackers your personally identifiable information (PII) that can be used for identity theft, you can contact TransUnion, Equifax, and Experian to freeze your credit. Doing this prevents scammers from using your information to take out loans or apply for new credit cards in your name.
Monitor your credit card and bank statements for suspicious transactions. You can also use identity theft protection services, including credit and PII monitoring. Advanced services include a feature that monitors social media for profiles created under your name and other services like stolen data restoration support or ID restoration process.
Also, make sure to download the latest software update or patch for your device as soon as they’re available, as these can help plug security vulnerabilities and ward off future attacks.