As one of the most popular website builders in the world, WordPress has yet again become a target for malware. Though security researchers are still trying to work out how certain sites became infected, there are ways to check if your WordPress site is one of the victims, and to defend against any imminent attacks.
Your WordPress Site May Have Some Nefarious Code
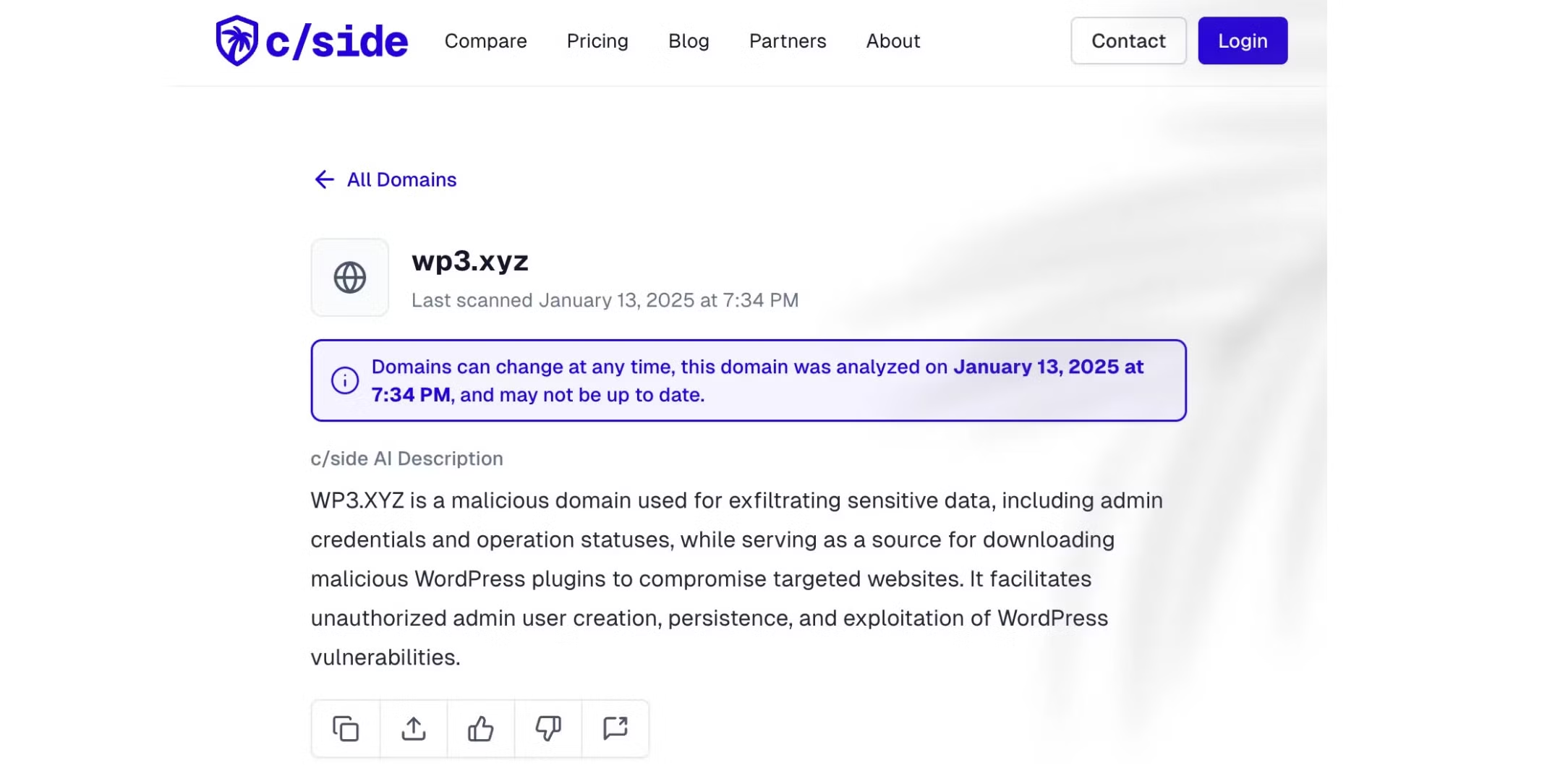
A team of security researchers for c/side, a cybersecurity company, reported that 5,000 WordPress sites were targeted in a recent malware campaign. According to the report on the c/side blog, the malicious domain known as WP3.XYZ is being “used for illustrating sensitive data, including admin credentials and operation statuses,” while also allowing malefactors to create unauthorized admin users. Subsequently, those false admins can download dangerous WordPress plugins to those vulnerable websites.
The good news is, activity such as unauthorized admin accounts can be spotted in the code, making it possible to review your site and remove them, along with any mysterious plugins.
How to See if Your Website Is Infected and Protected
If you have a WordPress site, you should check its security using one of the following resources:
If vulnerabilities are flagged, you should log in to your WordPress account to remove unused, suspicious plugins as well as unauthorized admins.
Whether or not your website was hit by the latest malware attack, you should still take steps to protect your WordPress site. For this attack specifically, you can quickly implement a safeguard by blocking the following domain in your firewalls or security tools:
https://wp3[.]xyz
In addition to blocking malicious domains like this one, you can also set up multifactor authentication (MFA) for your account. Lastly, you can add or double check that you have features in place that protect against Cross-Site Request Forgery (CSRF) attacks.
The research team at c/side is still investigating the origin of the malicious scripts, so we don’t yet know exactly where the vulnerability lied. That said, third-party plugins and website themes that aren’t properly built are often sources of malware. For this reason, it’s a good idea to check the sources of your plugins to ensure they’re well reviewed and trustworthy.
Cyber-vandalism like website defacement and web-based phishing attacks are unfortunate realities in our digital age, and it’s important to remain vigilant—even when it’s tempting to let your website sit idly while you focus on other areas of your business or personal life.